

Managed Detection and Response
MDR Core
Truesec’s SOC is the largest in the Nordics, our MDR Core solution provides 24/7 monitoring of your networks, endpoints, and cloud environments. This solution is ideal for for small and medium-sized organizations seeking rapid endpoint monitoring, compliance, specialized SOC-as-a-Service.
Managed Detection and Response
MDR Core Solution
MDR Core is a service that is tailored for effective and efficient digital protection.
24/7 Monitoring
Read more
Threat Detection and Response
Read more
Threat Detection and Response
Truesec Custom Detection Solution
Read more
Truesec Custom Detection Solution
Threat Hunting and Intelligence
Read more
Threat Hunting and Intelligence
Endpoint Detection and Response (EDR)
Read more
Endpoint Detection and Response (EDR)
Benefits of MDR Core
Cost Efficient Cybersecurity Solution
Fixed fee structure based on the number of endpoints, avoiding the complexities of data log-based pricing.
Easy Onboarding
Easy to obtain, easy onboarding, no lock-ins, and easy offboarding
Expert Threat Detection and Response
Utilizing advanced techniques and tools for effective identification and neutralization of cyber threats.
Compliance with Industry Regulations
Assistance in meeting various industry-specific data protection and privacy standards.
Truesec MDR
Onboarding step by step
01
Initial Consultation and Planning
Talk with our Managed Detection and Response Core specialists. We’ll get straight to the point, identify weak spots, and devise a clear, effective integration strategy that’s custom-fit for your organization’s security demands.
02
Contact and Escalation point are tested
This critical step ensures seamless information flow between our teams. We verify all contact points and escalation procedures to guarantee that communication during security incidents is efficient and effective.
03
Review, Approval, and Technical Deployment
Review the proposed integration plan, provide your input, and upon approval, we’ll initiate the technical deployment of the MDR platform atop your existing infrastructure, ensuring a disruption-free transition.
04
Training and Service Activation
Upon completing the initial setup, we initiate our comprehensive monitoring and response services. This marks the transition to the go-live phase, where our team begins providing real-time cybersecurity defense. This step ensures that your organization is fully protected from the outset, with our MDR Core service vigilantly guarding your digital assets 24/7.
05
Ongoing Engagement and Evolution
At MDR Core, our involvement in your cybersecurity journey extends far beyond the initial go-live phase. We recognize that cyber threats are constantly evolving, and so are your security needs. Our ongoing engagement is designed to adapt and respond to these changes. Our comprehensive portfolio of cybersecurity solutions and access to a wide range of expert consultants ensures that, as your organization grows and shifts, you have the option to explore additional services and expertise that align with your emerging security landscape, all under the reliable umbrella of Truesec.
Truesec MDR
How we make a difference
- 60%
- of small businesses fold within six month of a cyber attack
- 500k
- endpoints monitored and protected 24/7 for incidents and breaches
- 0
- business impacting incidents affecting Truesec MDR customers
- +13 900
- incidents disarmed in 2023 on IT and OT equipment
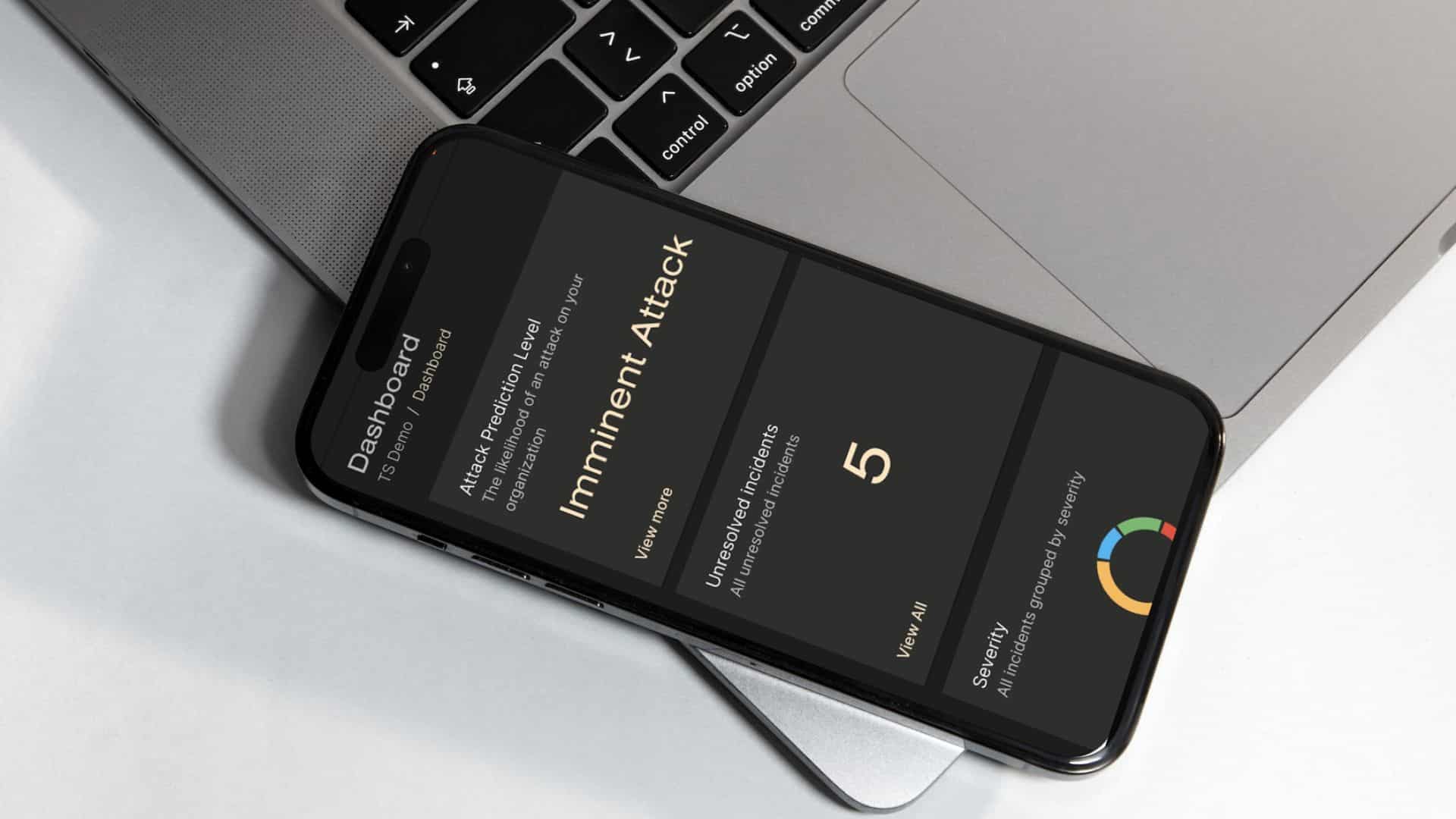
Truesec MDR
Truesec Cybersecurity Platform
We currently discover maybe 10-20 times more threats than before.
Get answers to your questions
An MDR overview
What is Managed Detection and Response (MDR)?
MDR is a comprehensive cybersecurity service that provides continuous monitoring, expert threat detection, and rapid response to secure your organization’s digital infrastructure. It focuses on protecting critical endpoints, servers, and client systems from cyber threats.

Who should consider using MDR ?
Our service is ideal for businesses that require robust cybersecurity but may not have the resources or expertise to manage an in-house Security Operations Center (SOC). MDR is suitable for organizations seeking enterprise-level security solutions that are both effective and cost-efficient.

How does MDR differ from traditional cybersecurity services?
MDR is not just a preventative tool; it’s a comprehensive solution. It includes 24/7 monitoring, advanced threat detection, proactive threat hunting, and response on true positives, all managed by our team of cybersecurity experts. This approach goes beyond traditional, passive defenses to offer active, continuous protection against cyber threats.

What types of threats can MDR detect and respond to?
MDR is equipped to handle a wide range of cyber threats, including malware, ransomware, phishing attacks, and advanced persistent threats (APTs). Our service is continuously updated to respond to the latest cyber threats.

Is MDR a fit for organizations with compliance requirements?
Absolutely. MDR assists organizations in meeting various industry-specific regulations related to data protection and privacy. Our service includes compliance-ready reporting and incident response capabilities.

What is the process for integrating MDR into my existing IT infrastructure?
Integration is streamlined and non-disruptive. Implementation is usually done in a few hours.

How is pricing for MDR determined?
Pricing for MDR is based on a fixed fee model, calculated on the number of endpoints (client computers + servers) in your organization. This approach makes understanding and managing costs easy without worrying about data log volumes or retention times.

What kind of support can I expect after implementing MDR?
Post-implementation, you will receive continuous support from our team, including the possibility to book a meeting with us to discuss questions or concerns, seek advice, or request additional services. Our support is not limited to reactive measures; we proactively engage with you to ensure that the MDR service continuously aligns with your evolving security needs and business objectives. In addition to direct support, you will have access to the Truesec Cybersecurity Platform. This online platform is a vital resource for managing your cybersecurity services with us.

How do I get started with MDR?
To begin, contact us at hello@truesec.com for an in-depth consultation. Our team will guide you through the onboarding process, ensuring a smooth and efficient transition to our MDR service.

How can I get started with Truesec’s Cyber Resilience Program service?
Reach out to us for an initial consultation to discuss your concerns, objectives, and existing cybersecurity framework. Together, we’ll lay the groundwork for a tailored Cyber Resilience Program implementation suited to your organization’s needs.

Forensic Analysis and Investigation
In this workflow, we initiate a forensic investigation to secure traces of the threat actor, determine if any company or personal data has been breached or exfiltrated, and determine what the threat actor has done within the environment. This determines in exact detail how the threat actor breached the system. We also conduct threat intelligence on the attackers by analyzing the dark web and locating other relevant leaked information.











